|
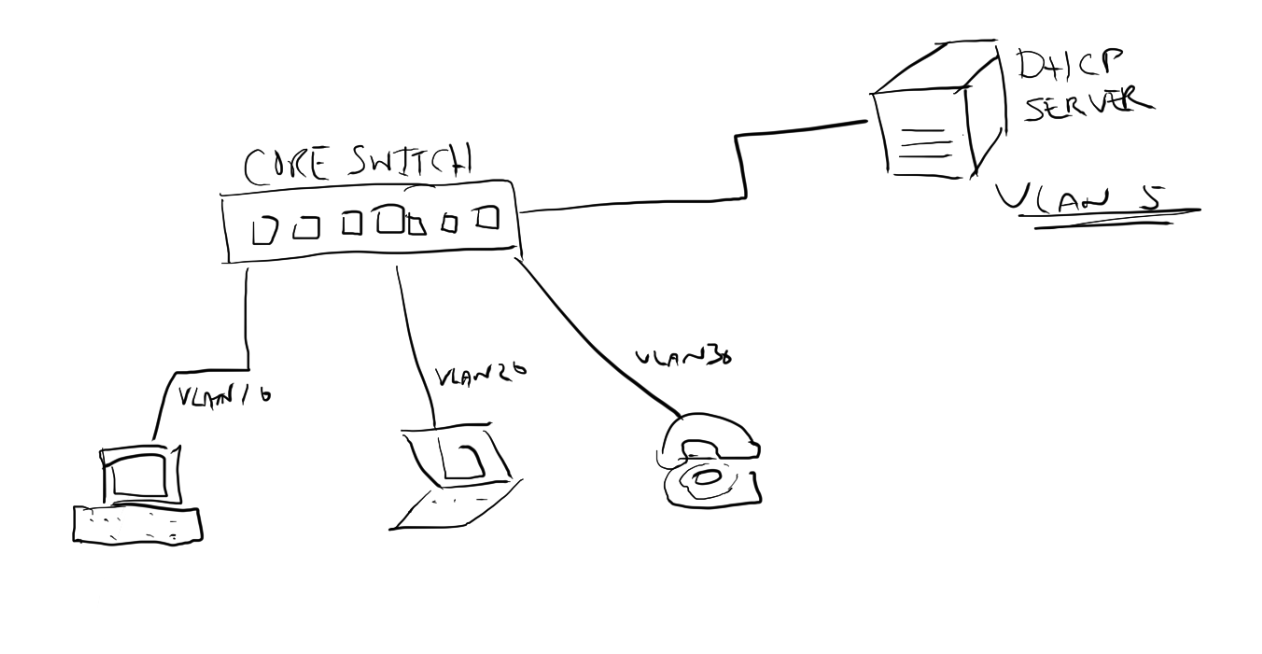
There are a bunch of features that are built in to network switches that generally go un-used because, simply, a switch will do it’s job right out of the box. After powering up a layer 2 or 3 switch managed switch and patching in computers and other network clients connectivity is achieved. But if that is all that is done then the wrong switch was purchased to begin with. Having a managed switch implies some configuration is likely to take place. The Layer 2 or 3 (or other) specification starts to indicate how much functionality is built in. Today, some features are are typically included across the board such as Spanning Tree or DHCP Snooping. DHCP-Snooping allows your switch to keep an eye out for DHCP responses to make sure they are coming from reliable sources, or to reduce the vectors in your network where a rogue DHCP server could operate. It does this by ensuring the DHCP responses from a server come from a trusted port and trusted IP address. It’s a simple mechanism that in simple networks could be an easy risk reduction tool - helping to reduce an attack vector. Network security should be important to us all, right? So it might not be an obvious risk to everyone. Whats the risk of multiple DHCP servers? Check out http://hakipedia.com/index.php/DHCP_Rogue_Server and for more detail go here: http://seclists.org/vuln-dev/2002/Sep/99  "Rogue DHCP servers can be stopped by means of intrusion detection systems with appropriate signatures, as well as by some multilayer switches, which can be configured to drop packets." How can you find a rogue DHCP server? Here is a quick youtube video showing how Wireshark can be used as a tool to identify a rogue DHCP server. Lets take a look at a simple configuration (performed in an HPE Aruba 3810M switch) in a network where the DHCP server is connected to switch port 10 and it’s IP address is 10.0.0.10: dhcp-snooping authorised-server 10.0.0.10 dhcp-snooping trust 10 dhcp-snooping You can see we set the server IP address 10.0.0.10 as an authorised server and trust port 10. Then dhcp-snooping enables the function. If you are using a switch or other devices as an ip helper or DHCP relay then you most likely will need to make that device an authorised DHCP server also in the DHCP Snooping configuration. Take the following network diagram as an example. The DHCP server is sitting on an entirely different network to the network devices that wish to obtain an IP address. Because DHCP is designed to work via broadcast frames on a single subnet the DHCP requests would never reach the server. This is where the switch IP Helper Address comes in. The switch will receive the DHCP requests on each of the client VLANs and forward the request on to the DHCP server. If the switch itself is not defined as an authorised server the frame returning from the DHCP server will not be forwarded on to client. Lets take a look at how DHCP-snooping should be configured for this network. dhcp-snooping authorised-server 10.0.0.10 dhcp-snooping authorised-server 10.0.10.1 dhcp-snooping authorised-server 10.0.20.1 dhcp-snooping authorised-server 10.0.30.1 dhcp-snooping trust 10 dhcp-snooping vlan 10 dhcp-snooping vlan 20 dhcp-snooping vlan 30 dhcp-snooping So here we have a configuration to authorise the DHCP server IP address and each of the interfaces within the switch for each VLAN. It’s this IP interface that will respond to DHCP requests from clients and therefore must be a trusted or authorised server. Switch port 10 is trusted as that is the uplink to the DHCP server. DHCP snooping is enabled on VLANs 10, 20 and 30 and the finally DHCP snooping is enabled. Note that if you have multiple hops to the DHCP server you should trust the uplinks (all in the case of redundant links) that will eventually lead to the DHCP server on switches further down the link chain. Configuration examples shown above are on Aruba switches (3810M and 2930F) running Aruba OS-switch version 16.03. This configuration will work across other HPE Aruba switches running similar software and is most likely the same configuration for older, non Aruba branded, HPE Pro-Curve switches. Microsoft TechNet Wiki article on How to Prevent Rogue DHCP Servers on your Network calls out the DHCP Snooping capability on network equipment https://social.technet.microsoft.com/wiki/contents/articles/25660.how-to-prevent-rogue-dhcp-servers-on-your-network.aspx * While some features may be considered common, it is always best to consult a product data-sheet or specifications documentation for each switch (or any networking products) when purchasing to ensure it does cover your requirements. While some features have been adopted as an industry standard others may be proprietary or have been implemented differently on one vendors product compared to another.
Comments
|
WifiHaxWe build and optimise networks. Continuous learning is our secret to being good. Along the learning journey we will share things here... Archives
May 2024
Categories
All
|

 RSS Feed
RSS Feed