|
Windows Netsh Commands
To see the SSIDs near the client netsh wlan show networks netsh wlan show networks interface=<NIC> netsh wlan show networks mode=bssid netsh wlan show networks mode=bssid >> c:\testfolder\wirelessclientdata.txt mode=bssid adds more details about each network Find an SSID with specific text in the name: netsh wlan show networks | find “Employee" or netsh wlan show networks | select-string <your-SSID-name> Show WLAN profiles configured in windows netsh wlan show profile Wireless LAN Driver Properties netsh wlan show driver
Comments
Python is the programming language to learn if you are a Network Engineer. It’s just one of the new skills you’re going to need to stay relevant and to be more than just a simple worker that adds no value beyond basic config.
With Python scripts you can repeat complex tasks in exactly the same way as many times as you like. You can build in variations so that the same job is dynamic when the need arises. For example you could deploy 20 access layer switches with identical configuration except each might have a unique management IP address. Think of the benefits of this type of automation at scale - 1000 switches by CLI is asking for trouble with misaligned configuration and it’s just down right inefficient use of time. Old school engineers would promote Perl for network scripts and automation - but its old school, less popular and harder to read. Python, as I understand it, can do anything Perl could do and is a much more accessible language in that it’s easier to read and begin working with. The use cases for scripting or programming will extend far beyond just replacing the legacy technique for the same tasks we perform today. The network is full of useful data that can be extracted for use elsewhere or to help inform the decisions for design tomorrow. All good technology products or services should contain an API which is a very easy way to have Python scripts interact with devices and software. Aruba Networks have released ArubaOS-CX on a core/aggregation switching platform that will allow Python scripts to run right on the switches. The analytics and automated troubleshooting capabilities show huge promise. I’ve been learning Python to perform some work in real life scenarios. If you can do it that way, like with most learning opportunities, you will be able to make better associations with the new skills you learn with the benefits of those skills in hobbies and work. Along the way I have been posting examples of my work in the Aruba Airheads Community, they are relevant to the Aruba Meridian solution. Using the Meridian API: Output Beacons info to CSV Using the Meridian API: Checking Beacon Battery Levels Using the Meridian API: Storing the JSON Output (Local Caching) Using the Meridian API: Caching Beacons Data in a file Using the Meridian API: Caching Maps Data in a file The posts include python files and a step by step break down describing the lines of programming so you can learn how they work. My hope is someone might either make use of the python scripts in their entirety or be able to use sections (or particular functions) for their own projects. There are so many resources around to help you to get started with Python. If you’re using a MacOS X as your computer operating system then Python is even pre-installed. There are countless books and paid or free online tutorials and courses. Now is the time to get some experience, see if there is any way you could take one of your current tasks and include a bit or Python training in to it. If you read this post by Steven Iveson in April 2013 you might feel a bit late to the game. There is no time like now to start. https://packetpushers.net/programming-101-for-network-engineers-why-bother/ Search the web for "python for network engineers" and you'll come across countless Udemy courses and other sources. Let me know if you find any good ones. In the old days if you wanted to do wireless protocol analysis you really needed some specialised equipment. An AirPcap USB interface was a pretty coveted device in the 2010's as it allowed for sniffing of 802.11n wireless frames directly in software like Wireshark on a Windows laptop. There was also AirMagnet Wi-Fi Analyzer that required a specific AirMagnet card and driver for packet analysis and Wi-Fi troubleshooting. The cost of these tools meant that it was difficult for the average Network Engineer to be readily equipped with such capabilities. Then it became widely known that Apple MacBooks were able to switch their built-in Wi-Fi interface to monitor mode for native wireless sniffing. MacOS quickly became a popular device of choice for Wireless Professionals but many of the applications required the Windows OS to run. The lack of dual OS support still left many needing multiple devices to complete their tool-kit. Many of the legacy applications that didn't bring support to MacOS eventually became obsolete. A good example of this is how AirMagnet Survey lost most of it's market share to Ekahau, which eventually brought out a MacOS version of it's Wi-Fi modelling and survey software.
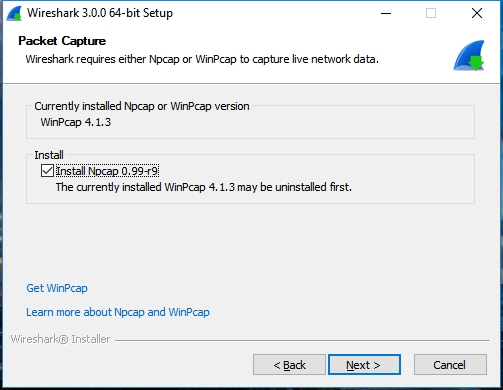
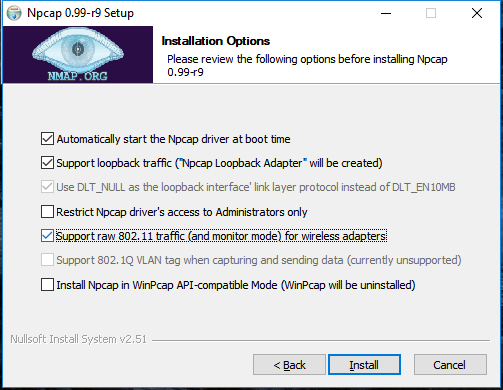
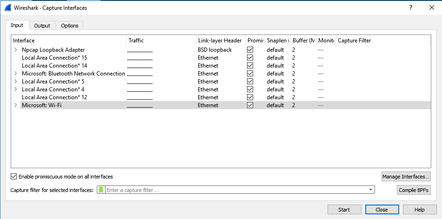
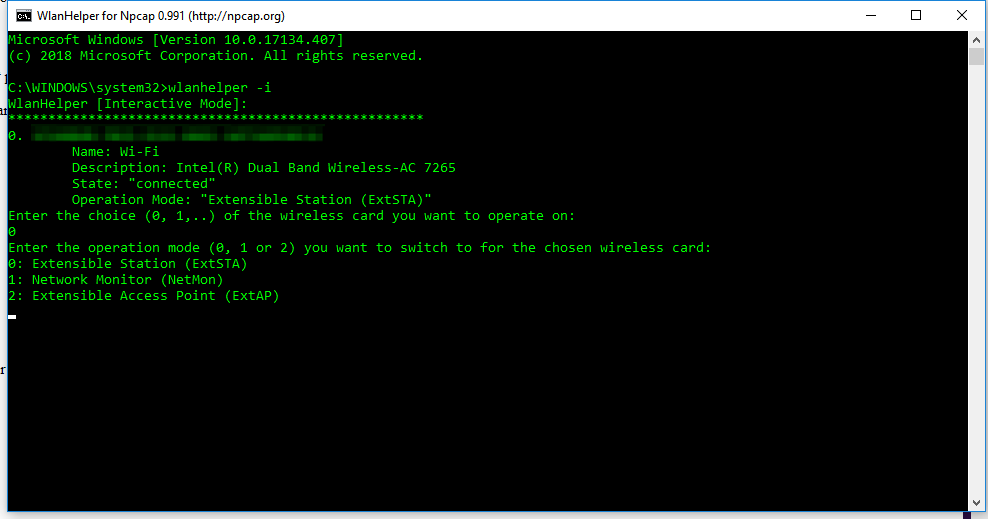
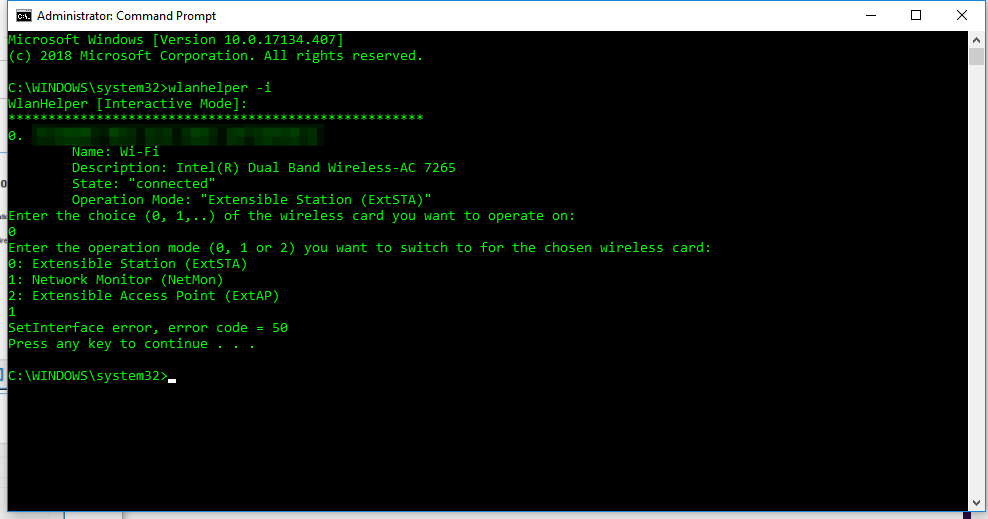
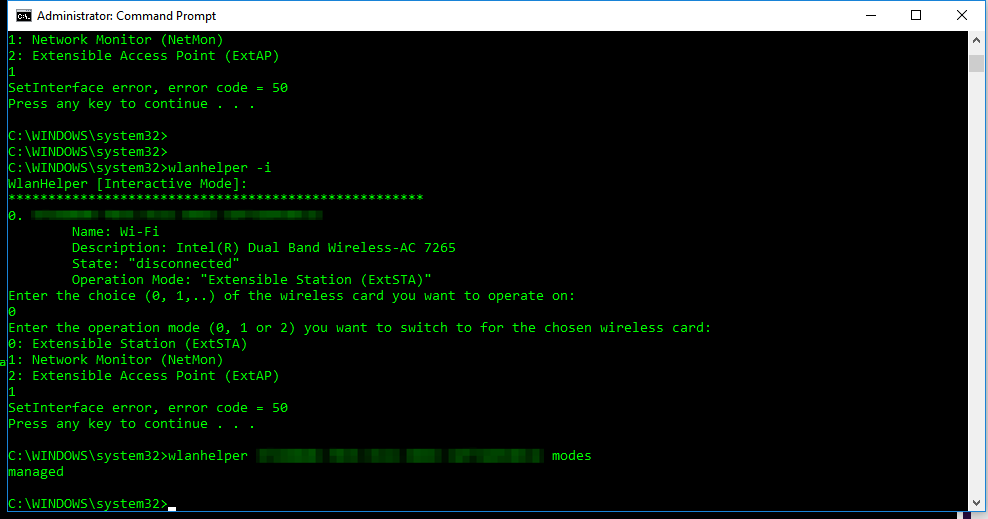
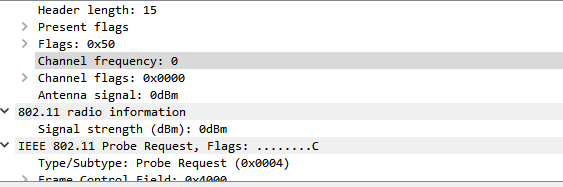
Wireshark 3.0.0 for Windows introduces a new capture driver that replaces the long standing WinPcap. It's amazing how long WinPcap has been around - I draw the indication of it's breadth of use from the Winpcap.org website. "Thanks to its set of features, WinPcap has been the packet capture and filtering engine for many open source and commercial network tools, including protocol analyzers, network monitors, network intrusion detection systems, sniffers, traffic generators and network testers. Some of these networking tools, like Wireshark, Nmap, Snort, and ntop are known and used throughout the networking community." Thanks WinPcap! We've seen some long hours together... Introducing Npcap. OK, so paying homage to a capture driver and welcoming it's replacement is pretty nerdy. I get it. But there is more too it (it gets nerdier). Take a peek at the installation options... The big one here is the support for raw 802.11 traffic monitoring! It's important to note some of the other items though... capturing loopback adapters can be really useful, restricting captures to Admin only could be strategically smart and providing backwards compatibility to applications that don't yet use the new driver but are expecting to still have access to WinPcap is just plain respectful. They're cool, but monitor mode in Windows takes the cake! So at this point of the install you might imagine my excitement. Well, it didn't turn out to be as straight forward as just installing Npcap. I was half hoping to just open Wireshark and tick the monitor box much like I can on my MacBook - No Dice! Off to the manual I go https://nmap.org/npcap/guide/npcap-users-guide.html#npcap-feature-dot11-wireshark - Wireshark only honours monitor mode when it is set within the Wireshark GUI but it's not available. So I read about the WLANhelper.exe tool where you can manually set monitor mode on an interface https://nmap.org/npcap/guide/npcap-devguide.html#npcap-feature-dot11 The first time I tried enabling monitor mode on my built-in NIC (Intel Dual Band Wireless-AC 7265) I got an error: I kept getting the error and found I could check the available modes for my wireless interface with the command: wlanhelper <nic guid> modes So it looks like the Intel 7265 can't do monitor mode. So what can? I found this list https://secwiki.org/w/Npcap/WiFi_adapters I do have a Savvius branded Netgear A6210. To get it recognised in Wireshark I installed the driver from the Netgear website and rebooted the laptop. I checked the wlanhelper.exe and verified the adapter existed there too. My first attempt to capture in monitor mode resulted in no packets. Second time round I disabled promiscuous mode and it worked a charm. As indicated in the Wi-Fi Adapters list this NIC doesn't pass down the Wi-Fi frequency so the radiotap header doesn't include info about the channel being captured so I had to hunt for that detail in a Beacon frame. The documentation doesn't make it apparent how you would change the frequency for the capture - there is an option command using the wlanhelper tool. Enable monitor mode for the NIC in wlanhelper wlanhelper <guid> mode monitor or use the wlanhelper -i interactive mode then set the channel wlanhelper <guid> channel 52 check the channel wlanhelper <guid> channel Wireshark will now be capturing from that channel as set. This can be set prior to capture or changed during a current capture.
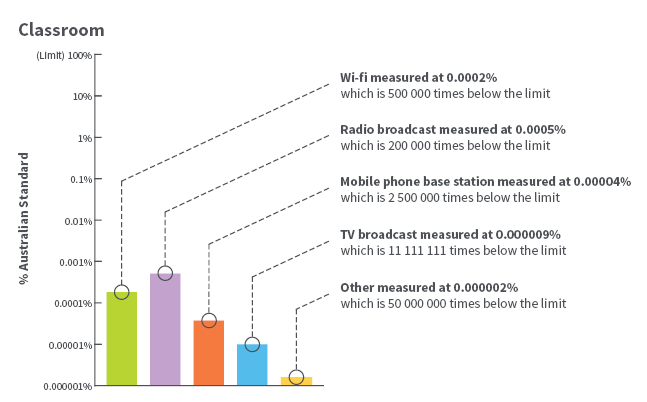
Happy capturing team! Download Wireshark here https://www.wireshark.org/#download Have you ever been asked if Wi-Fi is bad for our health? If you work with Wi-Fi you will have faced this question at least once, if not once every other month. There is a lot of misinformation, but lets not start with that. Recently I was asked to provide advice on the safety of Wi-Fi in regards to human health - this came up because I had made a recommendation to place Access Points underneath seats in a tiered seat (cinema style) theatre. The under-seat design is a story for another time. It occurred to me that the audience who had raised the concern of the proximity of Access Points to people would most likely be non-technical and would not had heard "The Spiel" before. I wanted to be as prepared as possible and armed with the most up to date information I could find. So I spent an entire Saturday reading through information - here is what I found. When reading about the effects of electromagnetic energy exposure it is important to note the radio frequencies of Wi-Fi are limited in range. Many of the studies and documents that are available relate to much wider frequencies (e.g. 0 - 300 GHz) or very targeted frequencies used in other technologies such as cellular base stations for mobile phones. The most common frequencies used for Wi-Fi occur between 2.4 GHz and 5.9 GHz. It is also important to note that the majority of Wi-Fi deployments will operate at a transmission power much lower to the services in other frequencies such as cellular, TV and Radio broadcast. While I've provided links to the various articles and content I have also included snippets for those who find it all a bit TLDR. Who's Who?ARPANSA - Australian Radiaton Protection and Nuclear Safety Agency Australian Government’s primary authority on radiation protection and nuclear safety. ARPANSA protect the Australian people and the environment from the harmful effects of radiation through understanding risks, best practice regulation, research, policy, services, partnerships and engaging with the community. ACMA - Australian Communications and Media Authority The independent statutory authority tasked with ensuring most elements of Australia's media and communications legislation, related regulations, and numerous derived standards and codes of practice operate effectively and efficiently, and in the public interest. ACMA is a 'converged' regulator, created to oversee the convergence of the four 'worlds' of telecommunications, broadcasting, radio communications and the internet. WHO - World Health Organisation The World Health Organization (WHO) is a specialized agency of the United Nations that is concerned with international public health. IEEE - Institute of Electrical and Electronics Engineers The IEEE Standards Authority is an organization within IEEE that develops global standards in a broad range of industries, including: power and energy, biomedical and health care, information technology and robotics, telecommunication among others. What They SayACMA: The ACMA and EME https://www.acma.gov.au/Citizen/Spectrum/About-spectrum/EME-hub/the-acma-and-eme The ACMA regulates EME from consumer devices such as mobile phones, baby monitors, cordless phones and smart meters with inbuilt antennas through the Radiocommunications (Compliance Labelling - Electromagnetic Radiation) Notice 2014 (the EME Labelling Notice) and the Radiocommunications (Electromagnetic Radiation-Human Exposure) Standard 2014 (the Human Exposure Standard). AMCA: Wi-Fi https://www.acma.gov.au/Citizen/Spectrum/About-spectrum/EME-hub/wifi The ACMA has found that EME exposure from Wi-Fi transmitters is significantly below the limits of the ARPANSA Standard. ARPANSA: Wi-Fi in Schools Measurement Study https://www.arpansa.gov.au/research/surveys/wi-fi-in-schools-measurement-study This study showed that the typical RF exposure of children from Wi-fi at school is very low and comparable or lower to other sources in the environment such as radio and TV broadcasts and mobile phone base stations. ARPANSA: Wi-Fi and Health https://www.arpansa.gov.au/understanding-radiation/radiation-sources/more-radiation-sources/wi-fi It is the assessment of ARPANSA and other national and international health authorities, including the World Health Organization (WHO), that there is no established scientific evidence of adverse health effects below current exposure limits. WHO: Electromagnetic Fields and Public Health http://www.who.int/peh-emf/publications/facts/fs304/en/ In fact, due to their lower frequency, at similar RF exposure levels, the body absorbs up to five times more of the signal from FM radio and television than from base stations. This is because the frequencies used in FM radio (around 100 MHz) and in TV broadcasting (around 300 to 400 MHz) are lower than those employed in mobile telephony (900 MHz and 1800 MHz) and because a person's height makes the body an efficient receiving antenna. Further, radio and television broadcast stations have been in operation for the past 50 or more years without any adverse health consequence being established. IEEE: Standard for Safety Levels with Respect to Human Exposure to Radio Frequency Electromagnetic Fields, 3 kHz to 300 GHz https://ieeexplore.ieee.org/document/1626482/ Federal Legislation: Radiocommunications (Electromagnetic Radiation - Human Exposure) Standard 2014 https://www.legislation.gov.au/Series/F2014L00960 The measurement methods to determine if the aware user device or non- aware user device meets the standard for performance in subsection 8 (1) or 8 (2) are the measurement methods identified in EN 62209-2 or IEC 62209- 2. A test report must comply with the requirements in EN 62209-2 or IEC 62209-2 which contained the measurement methods identified in accordance with subsection (2). WHO: Handbook on Establishing a Dialoge on Risks from Electromagnetic Fields http://www.who.int/peh-emf/publications/risk_hand/en/ Public Health England: Exposure to electromagnetic fields from wireless computer networks http://webarchive.nationalarchives.gov.uk/20140714093801tf_/http://www.hpa.org.uk/Topics/Radiation/UnderstandingRadiation/UnderstandingRadiationTopics/ElectromagneticFields/RadioWaves/WiFi/WiFiprojectreportonresultsSeptember2011/ The duty factor investigation shows that laptops and access points transmit for only small proportions of the time during typical lessons less than 1% of the time for laptops and less than 12% for access points. This means that the time-averaged exposure arising from the use of laptops in schools is even lower than those when laptops were measured under controlled conditions in the laboratory, and the SARs will also be smaller than those estimated above. Who Else Shares InformationThe Wi-Fi Alliance and Wi-Fi equipment manufacturers (aka Vendors) also submit perspectives and points of information to the mix. I deliberately leave material sourced from these organisations to last as it is, in most cases, referencing other material already covered by other organisations. It's also worth noting that both vendors and the Wi-Fi Alliance have an obvious bias towards finding and presenting the positive side of the story. It is my opinion that the Wi-Fi Alliance should not be considered a reliable source for health or medical based information. Vendor information should be followed for safe use and operation guidelines but like information from the Wi-Fi Alliance should not be used as the basis for medical advice. WFA - Wi-Fi Alliance Wi-Fi Alliance defines innovative, standards-based Wi-Fi technologies and programs, certifies products that meet quality, performance, security, and capability standards, provides industry thought leadership, and advocates globally for fair spectrum rules. WFA: Wi-Fi® and Health/Safety Brochure https://www.wi-fi.org/download.php?file=/sites/default/files/private/Wi-Fi_and_Health_Brochure_2015_0.pdf The wireless industry continually monitors information about RF health and related regulatory or policy changes to stay informed of up-to-date research and to be sure that the public can continue to have confidence in the safety of its products. In addition, Wi-Fi Alliance® supported two independent research studies both published in Health Physics, a peer-reviewed scientific journal. The first was an independent exposure study that conducted 356 measurements at 55 sites (including schools and hospitals) in four countries around the world. This study concluded that in all cases, the measured Wi-Fi signal levels were very far below international exposure limits (IEEE C95.1-2005 and ICNIRP) and in nearly all cases, far below other RF signals in the same environments. WFA: Wi-Fi and Health https://www.wi-fi.org/wi-fi-and-health Due to the ubiquity of Wi-Fi technology, questions about the safety of radio waves and Wi-Fi devices tend to arise from time to time. The wireless industry takes these concerns very seriously. Aruba’s Position on Health Concerns associated with Radio Frequency Exposure from WiFi https://arubapedia.arubanetworks.com/arubapedia/images/4/43/Aruba_Statement_on_WiFi_Health_Concerns.pdf Aruba is committed to providing products which are safe for our customers to own and use. Aruba’s wireless products are tested to ensure that they meet international RF safety standards. RF safety standards are regularly reviewed against the latest scientific studies to ensure they continue to protect the public’s health. Aruba: Regulatory Compliance and Safety Information Guide (AP-320) http://support.arubanetworks.com/Documentation/tabid/77/DMXModule/512/Command/Core_Download/Method/attachment/Default.aspx?EntryId=21410 RF Radiation Exposure Statement: This equipment complies with FCC RF radiation exposure limits. This equipment should be installed and operated with a minimum distance of 7.87 inches (20cm) between the radiator and your body for 2.4 GHz and 5 GHz operations. Aruba: HPE Safety and Compliance Information Guide http://support.arubanetworks.com/Documentation/tabid/77/DMXModule/512/Command/Core_Download/Method/attachment/Default.aspx?EntryId=26048 Exposure to Radio Frequency Radiation: The radiated output power of this device is below the FCC radio exposure limits. Nevertheless, the device should be used in such a manner that the potential for human contact during normal operation is minimized. To avoid the possibility of exceeding the FCC radio frequency exposure limits, human proximity to the antennas should not be less than 20 cm (8 inches) during normal operation. What's Next?There is always a possibility that the organisations referenced above will adopt new testing or theories which bring a different perspective. I recommend you stay informed and periodically review the information available. If you do find what I've shared here useful please let me know with a comment below.
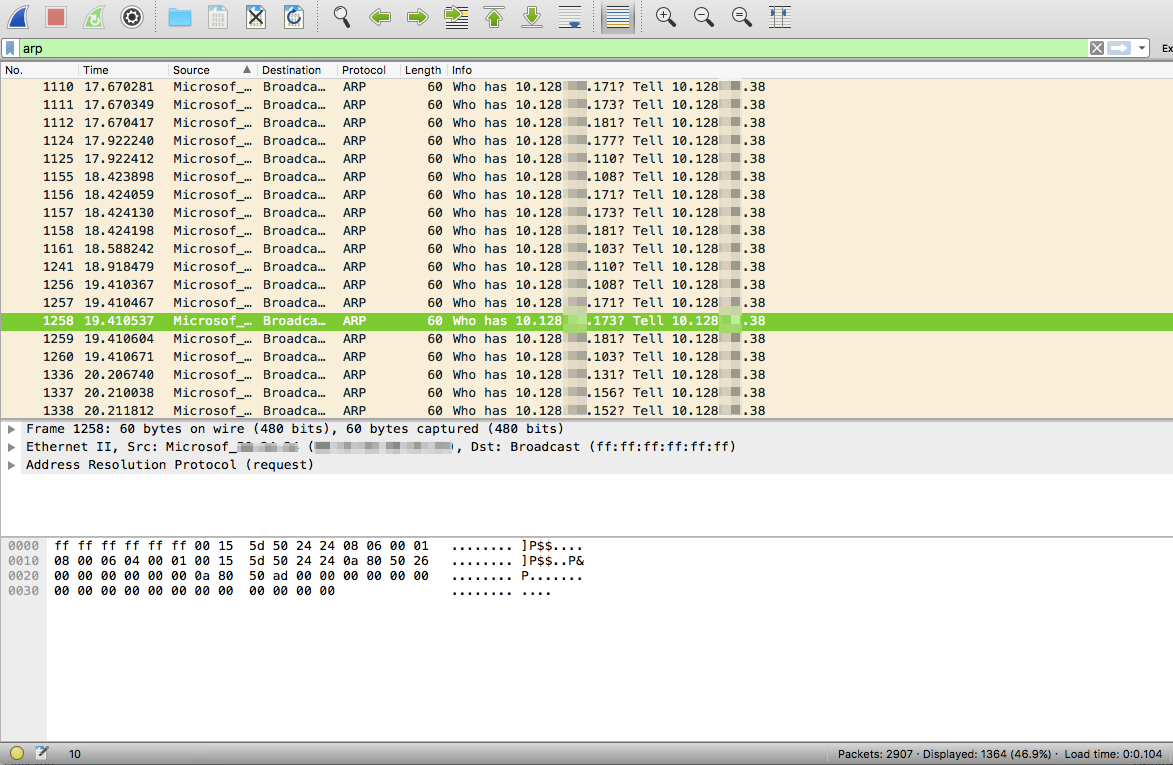
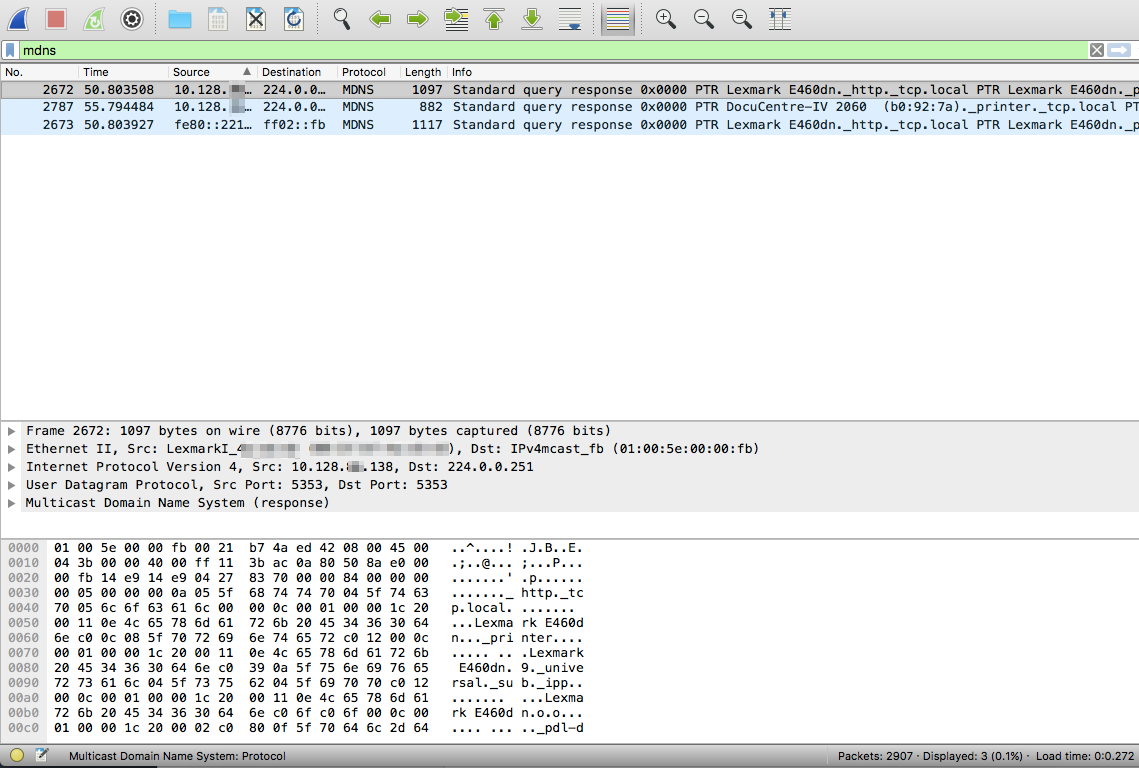
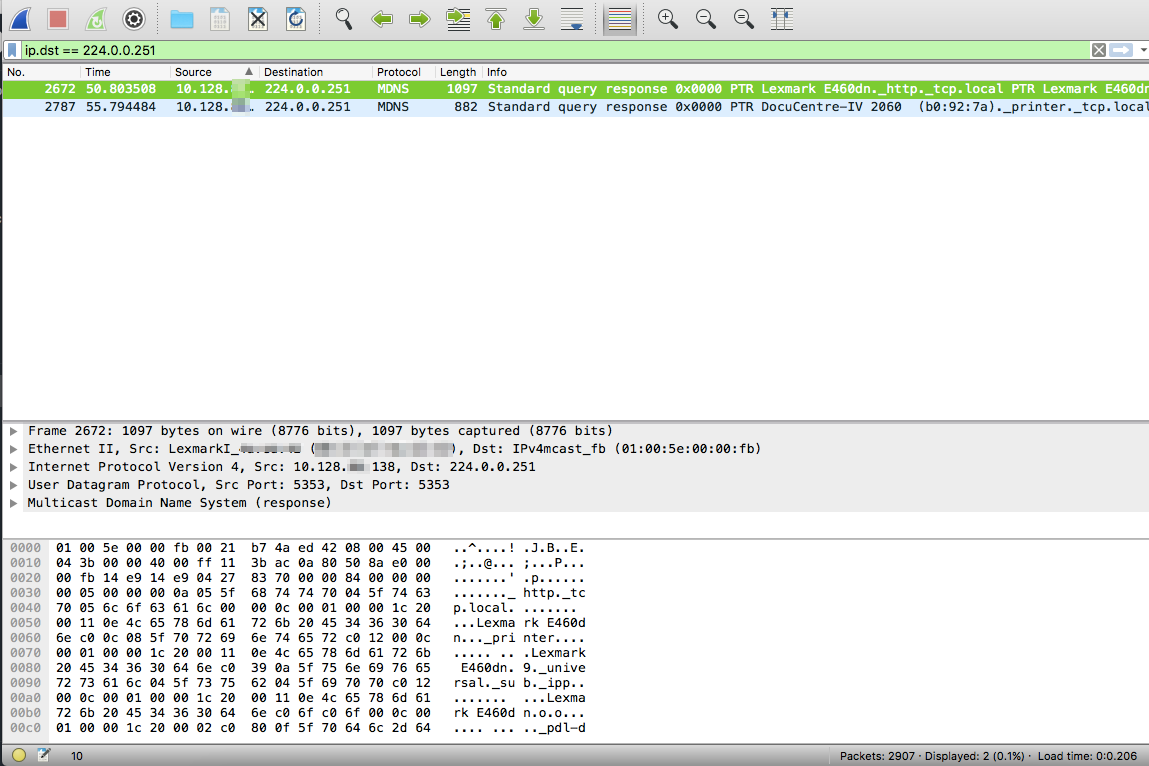
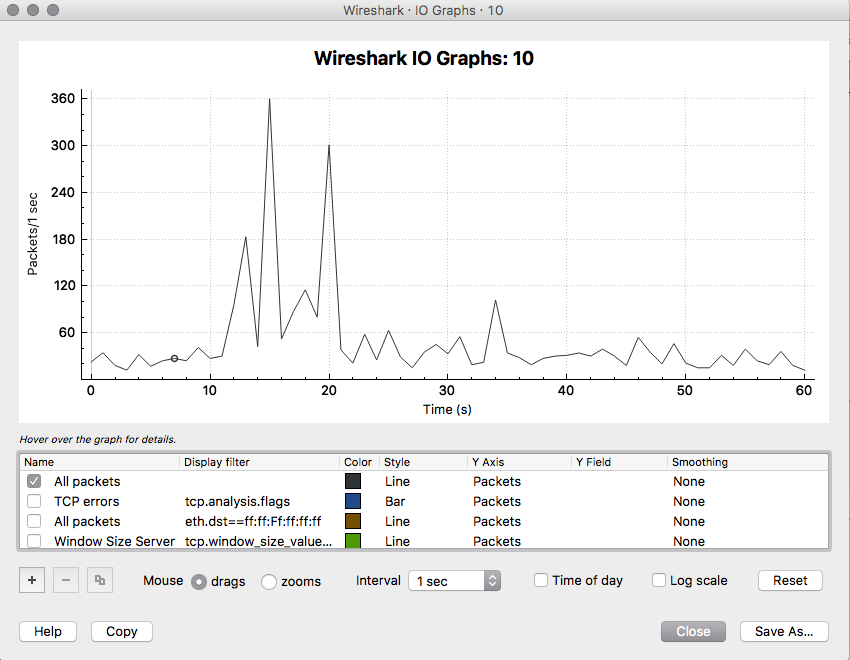
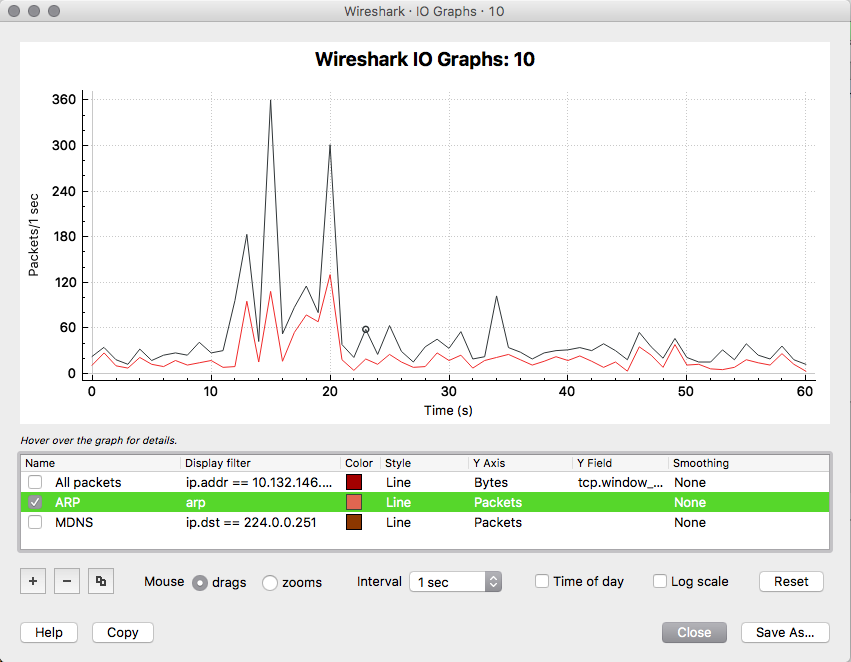
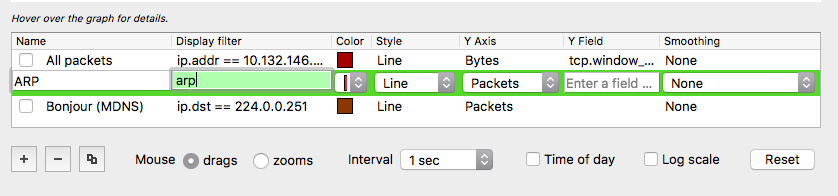
Wireshark is super powerful! You just need to learn how to increase your chances of finding needles in haystacks. Needles are the packets and frames which hold the forensic truth of what actually happened, the haystack is the rest of the junk packets and frames that usually get scooped up in the process of the capture. Here are a couple of easy steps to filter both in detail and visually for some interesting types of packets. Filtering for ARP frames in Wireshark is simple. For an existing packet capture just type arp and hit enter/return in the display filter bar. The corresponding packets will show only ones with the protocol type of ARP. to edit. Filtering for MDNS is equally as simple. In the display filter bar you can type mdns which will filter the displayed packets to those that match the protocol of MDNS. If you would like to isolate to Apple Bonjour specifically you can write a display filter for packets with a destination IP address of 224.0.0.251 as displayed below. Once we know how to display specific types of packets in Wireshark we can display those packets in graphs and see their relation to each other. I really like using the I/O Graph function of Wireshark to see the relative percentage of ARP or MDNS packets to the total number of packets in a visual way. To get to the I/O Graph click on Statistics in the Menu bar and find I/O Graph. Typically the I/O Graph will open displaying a line graph which represents the packets per second over time like below: By including extra details using the display filters previously mentioned you can get a visual representation of the number of ARP packets vs the total number of packets per second. On a quiet network (overnight when no one is around) the ARP protocol might be pretty much the only type of traffic present as devices keep their ARP tables up to date. But during the day you don't want ARP to be a huge percentage of traffic on your main client network segment - this might indicate an issue which would need to be further investigated. To differentiate between the quiet and busy times on your network it is worth taking some sample captures from various points on the network and analysing the packets per second to see what is 'expected' or 'normal'. The more you look at it the more understanding you will get for the norms in your environment. To include this you simply add an additional graph detail by clicking the Plus button below the graph details pane and entering a new display filter with a customised name: Be sure to colour your new line in a different colour so you can easily see the difference between it and other lines on the graph. Wireshark can be used in the same way for 802.11 frame captures. For example you might be able to display broadcast frames vs total frames per second within the I/O Graph, or maybe visualise management and control frames vs data frames. As you learn more display filters the I/O Graph function of Wireshark can become very powerful.
|
WifiHaxWe build and optimise networks. Continuous learning is our secret to being good. Along the learning journey we will share things here... Archives
May 2024
Categories
All
|

 RSS Feed
RSS Feed